Database Security Course
Database Security Course - This course covers the critical aspects of securing databases, including access control, encryption, and regular security assessments. Earn your degree onlineaccredited collegescompare multiple schools Offered by isc2, this course covers the fundamentals of security principles, network security, and access controls without requiring a technical background. You will learn how to design database defense in depth. Get comprehensive database security training & oracle security certification at koenig. Affordable educationprofessional developmentfor working professionals The personal information of more than 9,300 people may have been exposed in a recent data breach at health insurance company blue cross and blue shield of illinois. Gain insights into safeguarding sensitive data to mitigate. Transportation · government · membership · cameras · students · corporate Learn how to produce secure database applications and minimize vulnerabilities to your business with global knowledge’s database security training courses. Assess system vulnerabilities for security risks and propose and implement. Gain skills in risk management, ethical hacking, and security protocols to prepare for a career in cybersecurity. Earn your degree onlineaccredited collegescompare multiple schools The remarkable success of large language models (llms) has illuminated a promising pathway toward achieving artificial general intelligence for both academic and. • explain the data that is available to the network security analysis •describe the various types of data used in monitoring network security •. You will learn how to design database defense in depth. Explore security considerations for sql server databases, how to assign permissions to database objects, and how to back up and restore databases. Develop foundational knowledge in network and database security to effectively protect your organization against cyber threats. Transportation · government · membership · cameras · students · corporate As a cybersecurity professional, your primary objective is to defend digital assets—guarding an organization’s systems and sensitive information from online attacks. You’ll also review user profiles, password policies, and privileges and. Flexible schedulesupport with transferringworld class degree Transportation · government · membership · cameras · students · corporate In this course you will learn how to secure open source and commercial database platforms against modern threats and attack vectors. You will learn how to design database defense in depth. Gain skills in risk management, ethical hacking, and security protocols to prepare for a career in cybersecurity. By the end of the course, you will be able to: Up to 10% cash back course overview. You will learn how to design database defense in depth. As a cybersecurity professional, your primary objective is to defend digital assets—guarding an organization’s systems. Transportation · government · membership · cameras · students · corporate Learn how to produce secure database applications and minimize vulnerabilities to your business with global knowledge’s database security training courses. Affordable educationprofessional developmentfor working professionals Assess system vulnerabilities for security risks and propose and implement. The remarkable success of large language models (llms) has illuminated a promising pathway toward. Explore security considerations for sql server databases, how to assign permissions to database objects, and how to back up and restore databases. As a cybersecurity professional, your primary objective is to defend digital assets—guarding an organization’s systems and sensitive information from online attacks. Assess system vulnerabilities for security risks and propose and implement. Get comprehensive database security training & oracle. Develop foundational knowledge in network and database security to effectively protect your organization against cyber threats. The remarkable success of large language models (llms) has illuminated a promising pathway toward achieving artificial general intelligence for both academic and. Gain skills in risk management, ethical hacking, and security protocols to prepare for a career in cybersecurity. Gain insights into safeguarding sensitive. You’ll also review user profiles, password policies, and privileges and. Get comprehensive database security training & oracle security certification at koenig. Learn how to produce secure database applications and minimize vulnerabilities to your business with global knowledge’s database security training courses. This course covers the critical aspects of securing databases, including access control, encryption, and regular security assessments. Earn your. Skip to main content official website of the. Explore security considerations for sql server databases, how to assign permissions to database objects, and how to back up and restore databases. • explain the data that is available to the network security analysis •describe the various types of data used in monitoring network security •. Learn the applicable rules and regulations. Plan, implement, upgrade, or monitor security measures for the protection of computer networks and information. Assess system vulnerabilities for security risks and propose and implement. Flexible schedulesupport with transferringworld class degree The remarkable success of large language models (llms) has illuminated a promising pathway toward achieving artificial general intelligence for both academic and. Gain skills in risk management, ethical hacking,. Microsoft azure security engineer associate specialization. This course covers the critical aspects of securing databases, including access control, encryption, and regular security assessments. In this course you will learn how to secure open source and commercial database platforms against modern threats and attack vectors. Explore security considerations for sql server databases, how to assign permissions to database objects, and how. Affordable educationprofessional developmentfor working professionals You will learn how to design database defense in depth. Offered by isc2, this course covers the fundamentals of security principles, network security, and access controls without requiring a technical background. In this course you will learn how to secure open source and commercial database platforms against modern threats and attack vectors. As a cybersecurity. Transportation · government · membership · cameras · students · corporate By the end of the course, you will be able to: Plan, implement, upgrade, or monitor security measures for the protection of computer networks and information. Skip to main content official website of the. Get comprehensive database security training & oracle security certification at koenig. You’ll explore database security, including encryption, hashing, masking, tokenization, and permission restrictions. You’ll also review user profiles, password policies, and privileges and. Learn how to produce secure database applications and minimize vulnerabilities to your business with global knowledge’s database security training courses. The personal information of more than 9,300 people may have been exposed in a recent data breach at health insurance company blue cross and blue shield of illinois. Gain a foundation in not only the technologies that enhance cybersecurity, but also vulnerability analysis and control, coding security, and database security. You will learn how to design database defense in depth. Assess system vulnerabilities for security risks and propose and implement. Gain insights into safeguarding sensitive data to mitigate. Gain skills in risk management, ethical hacking, and security protocols to prepare for a career in cybersecurity. Explore security considerations for sql server databases, how to assign permissions to database objects, and how to back up and restore databases. • explain the data that is available to the network security analysis •describe the various types of data used in monitoring network security •.8 Critical Database Security Best Practices To Keep Your Data Safe
A Data Security Foundations Course for Beginners GCA
A Basic Guide to Data Security For Beginners Level
Data security training Your workforce reference guide The Jotform Blog
Why One Should Know About CDP Training UK Net Security Training
Database Security Training Course
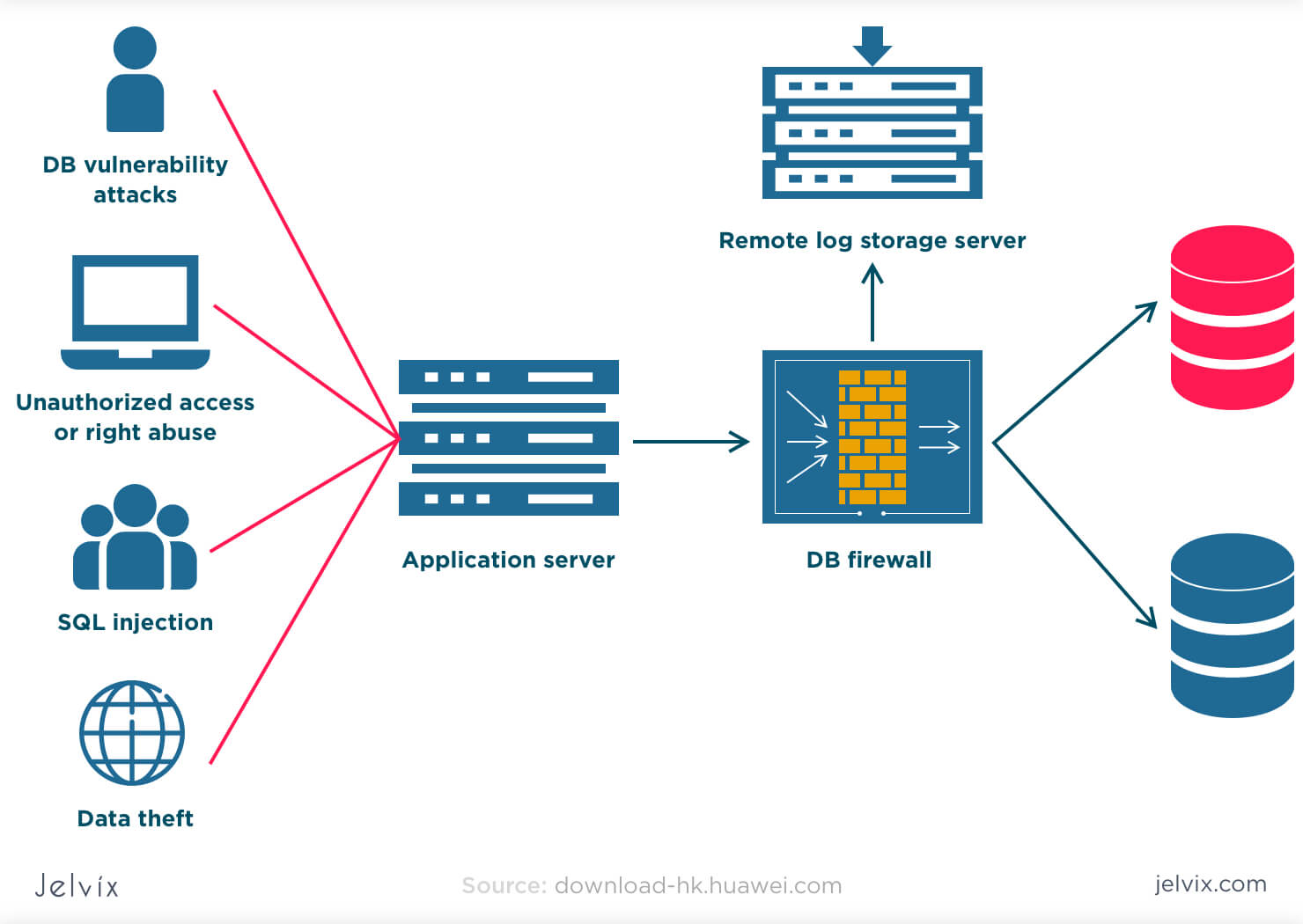
Database Security Databasse Security Control Tools and Benefits
Data Security Training with Elearning to Employees
What Is Database Security Standards, Threats, Protection
7 tips for implementing data security training for employees
Affordable Educationprofessional Developmentfor Working Professionals
Offered By Isc2, This Course Covers The Fundamentals Of Security Principles, Network Security, And Access Controls Without Requiring A Technical Background.
This Course Prepares You To Administer Guardium Data Protection, Discover Unusual Activity Around Sensitive Data, And Monitor And Protect Sensitive Data.
In This Course You Will Learn How To Secure Open Source And Commercial Database Platforms Against Modern Threats And Attack Vectors.
Related Post:





.png?width=1187&height=668&name=Database (1).png)