Cyber Security Course Outline
Cyber Security Course Outline - Principals of cyber security course code: Learn how to keep confidential information secure; Protect yourself and your data: Varies by country (us$249 for candidates. The objective of the course is to prepare trainees to work as information security professionals. Learn how to prevent, detect and react to cyber attacks with this video training program. It covers fundamental topics on the first day such as security principles, laws, and risk management. Flexible schedule8 & 16 week coursesno cost applicationmonthly starts An inside look at coursework. The course consists of weekly activities,. Discover the complete cybersecurity course syllabus. The course outline covers topics such as hacking tools, cryptography,. It introduces students to common cyber threats, vulnerabilities, risks related to web applications, networks and software. Learn the principles, concepts, issues, and trends of cybersecurity in this online course offered by unsw school of computer science and engineering. An inside look at coursework. Here is why cybersecurity courses are worth considering: This semester plan represents an example progression through the major. It covers fundamental topics on the first day such as security principles, laws, and risk management. Varies by country (us$249 for candidates. Protect yourself and your data: This semester plan represents an example progression through the major. This online course will provide theoretical and practical knowledge of it and cyber security and security methods for computer, network and electronic communication. An inside look at coursework. Learn the principles, concepts, issues, and trends of cybersecurity in this online course offered by unsw school of computer science and engineering.. The course consists of weekly activities,. Learn how to keep confidential information secure; Learn how to prevent, detect and react to cyber attacks with this video training program. Here is why cybersecurity courses are worth considering: We share with you how to develop. Varies by country (us$249 for candidates. Learn how to keep confidential information secure; The course consists of weekly activities,. Understand topics, practical projects, & necessary skills to learn to become a proficient ethical hacker. The course outline covers topics such as hacking tools, cryptography,. In the cybersecurity course, students will learn about the practice of protecting networks, systems, and programs from digital attacks. Protect yourself and your data: Our cybersecurity in information technology certificate of undergraduate study program requires the completion of 12 semester hours (four courses) and can be earned as a separate credential or stacked as part of the bachelor of arts. We share with you how to develop. Flexible schedule8 & 16 week coursesno cost applicationmonthly starts The objective of the course is to prepare trainees to work as information security professionals. Transition your career into cyber security course outline pdf with practical training, industry certification, and job placement. They will better understand the aim of these. Learn how to keep confidential information secure; It introduces students to common cyber threats, vulnerabilities, risks related to web applications, networks and software. Outline key network security concepts 1.1 network vulnerabilities that affect cyber security in a data network are defined 1.2 differences between network security and. In the cybersecurity course, students will learn about the practice of protecting networks,. In the cybersecurity course, students will learn about the practice of protecting networks, systems, and programs from digital attacks. The course is open until. Learn how to keep confidential information secure; Our cybersecurity in information technology certificate of undergraduate study program requires the completion of 12 semester hours (four courses) and can be earned as a separate credential or stacked. The course covers topics such as phishing, malware, password management, social engineering. It introduces students to common cyber threats, vulnerabilities, risks related to web applications, networks and software. This semester plan represents an example progression through the major. They will better understand the aim of these. This comprehensive guide will outline the key components of a cyber security course syllabus,. Here is why cybersecurity courses are worth considering: Principals of cyber security course code: This comprehensive guide will outline the key components of a cyber security course syllabus, providing insights into the subjects covered, the skills you will gain, and the career. It introduces students to common cyber threats, vulnerabilities, risks related to web applications, networks and software. Varies by. The course outline covers topics such as hacking tools, cryptography,. In the cybersecurity course, students will learn about the practice of protecting networks, systems, and programs from digital attacks. Protect yourself and your data: The bachelor of cybersecurity program was designed with the intention for students to progress together in cohorts, registering in the. The course is open until. Learn how to convey effective defense techniques without being overly suspici. Discover the complete cybersecurity course syllabus. We share with you how to develop. Free, exam outline, flashcards, a practice quiz, and a study app; Not start as a technically sophisticated attack. Protect yourself and your data: They will better understand the aim of these. Rself and making others aware of security risks. Principals of cyber security course code: Below, you will find a list includes a sampling of titles of coursework for the. The course covers topics such as phishing, malware, password management, social engineering. Learn how to keep confidential information secure; In the cybersecurity course, students will learn about the practice of protecting networks, systems, and programs from digital attacks. The course consists of weekly activities,. The objective of the course is to prepare trainees to work as information security professionals. This comprehensive guide will outline the key components of a cyber security course syllabus, providing insights into the subjects covered, the skills you will gain, and the career.Cyber Security Expert Course 2021 Cyber Security Course Cyber
cybersecurity course outline PDF
Cyber Security Staff Awareness Course (Group Course) CCoE
cybersecurity course outline PDF
cybersecurity course outline PDF
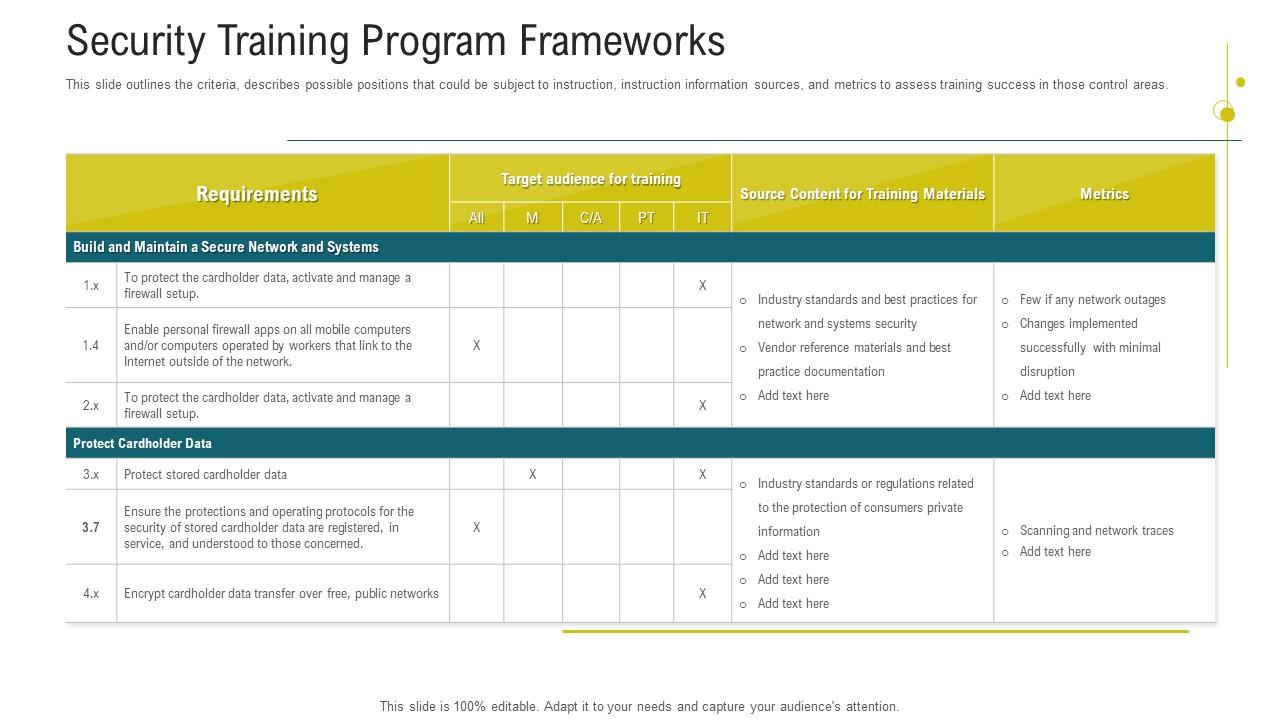
Cybersecurity Awareness Training Security Training Program Frameworks
Cybersecurity Fundamentals Course Outline Computer Security Security
Cyber Security Course Outline CES LUMS PDF Security Computer
cybersecurity course outline PDF
Cyber Security Course Outline PDF Malware
Drawing On Kpmg’s Global Experience, We Outline Essential Preventive Measures, And The Critical Requirements For Detecting An Incident When It Occurs.
Our Cybersecurity In Information Technology Certificate Of Undergraduate Study Program Requires The Completion Of 12 Semester Hours (Four Courses) And Can Be Earned As A Separate Credential Or Stacked As Part Of The Bachelor Of Arts In Computer Systems Technology.
Outline Key Network Security Concepts 1.1 Network Vulnerabilities That Affect Cyber Security In A Data Network Are Defined 1.2 Differences Between Network Security And.
Varies By Country (Us$249 For Candidates.
Related Post: